
The National Institute of Standards and Technology (NIST) has raised the bar with its newly released Cybersecurity Framework 2.0. This iteration emphasizes that cybersecurity is not merely an IT issue—it is a central business risk that demands active oversight by executive leadership. At CDA, we welcome this shift, which aligns with our own view, which is that organizations must approach cybersecurity with a governance-first, risk-based mindset.
✅ What’s New in NIST CSF 2.0?
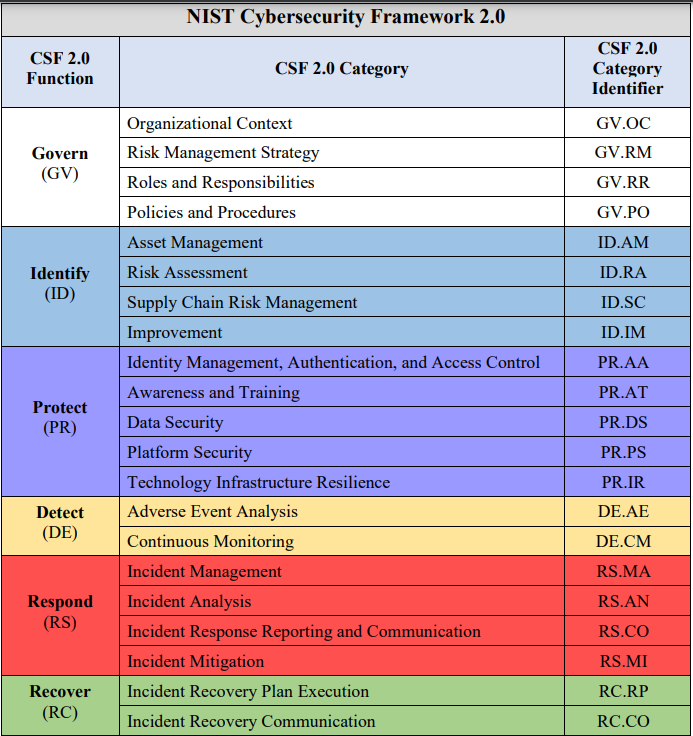
While the original framework introduced the now-famous core functions—Identify, Protect, Detect, Respond, and Recover—CSF 2.0 extends these with a stronger focus on the ‘Govern’ function. This enhancement directly calls on executive management and boards to take responsibility for establishing cybersecurity policies, overseeing program performance, and aligning security practices with enterprise risk management (ERM) strategies.
🛡️ Identifying Risk: The Foundation of Cybersecurity Governance
To govern cybersecurity effectively, leadership must first understand what they are protecting. Begin with a comprehensive Risk Assessment. Map out your IT assets—including systems, applications, data, and infrastructure—and assess their vulnerabilities, threat exposure, and business value.
This process allows executives to:
– Understand what assets are most critical to business continuity
– Pinpoint vulnerabilities that require immediate attention
– Quantify risks in operational, financial, and reputational terms
– Make informed decisions on cybersecurity investments
🔐 Building a Protection Strategy: Training, Tech, and Third-Parties
Protecting IT assets is not just about firewalls and encryption. NIST CSF 2.0 and real-world incidents highlight the need for a multilayered approach:
- **Train and empower your workforce**:
Cyber awareness is key to reducing human error, a major contributor to breaches. - **Vet your vendors**:
Ensure third-party providers comply with your security policies, especially as outsourcing grows. - **Deploy robust technology**:
Use AI-enabled SIEM, IDS/IPS, and EDR/XDR to proactively monitor and contain threats. - **Document clear responsibilities**:
Each stakeholder must understand their role in protecting digital assets.
🚨 Detection and Response: From Signal to Action
Having detection capabilities is critical—but knowing how to respond is equally vital. Incident management should be guided by predefined processes:
– Classify incidents by severity and impact
– Activate communication protocols with internal and external teams
– Involve forensic experts to identify root causes
– Conduct Business Impact Analyses (BIA) to assess fallout
– Apply lessons learned to strengthen future response
Managed Detection and Response (MDR) providers can support organizations that lack in-house capacity, ensuring real-time visibility into malicious activities.
🔄 Recovery and Business Resilience
Post-incident recovery is not simply about restoring systems. It’s about restoring trust and ensuring long-term continuity.
– Develop and test Recovery Playbooks regularly
– Define clear SLAs for recovery time and data restoration
– Delegate roles and responsibilities in advance
– Validate the integrity of backups and ensure data hasn’t been corrupted
– Communicate status updates to stakeholders and customers
🧠 Threat Modeling: From Awareness to Prevention
Threat Modeling is an essential practice in proactive risk reduction. It helps visualize how attackers may exploit systems and where defensive controls must be placed.
Steps include:
– Define business and security objectives
– Identify assets, entry points, and trust boundaries
– Decompose applications and infrastructure into flows and dependencies
– Analyze threats using STRIDE or PASTA methodologies
– Prioritize countermeasures and simulate scenarios
This approach ensures that your architecture, APIs, and integrations are secured end-to-end.
🔐 The CI4AM Security Objectives
Threat Modeling must align with the CI4AM principles:
– **Confidentiality**: Ensure only authorized access to sensitive data
– **Integrity**: Prevent unauthorized changes to systems and data
– **Availability**: Keep services running during incidents or failures
– **Authentication & Authorization**: Verify identities and manage access rights
– **Auditing**: Maintain traceable logs for compliance and investigation
– **Management**: Centralize control for scalable and consistent application
📄 What Executives Must Include in SLAs and Governance Plans
Effective governance isn’t just internal—it extends to vendor and third-party agreements. Your SLAs should include:
– Defined uptime and response time targets
– Security incident reporting procedures
– Third-party compliance and certification requirements (e.g., SOC 2, ISO 27001)
– Access control responsibilities and audit rights
– Legal liability and breach remediation clauses
– Periodic risk review meetings and escalations
🧩 What Curinovis Digital Agency Recommends
To get you through with the adoption of this revised framework, Curinovis Digital Agency can get guide in:
– Executive cybersecurity strategy workshops
– Risk assessment and Business Impact Analysis facilitation
– Vendor SLA reviews and contract optimization
– Threat Modeling sessions across software, network, and infrastructure
– Development of Recovery Playbooks and awareness programs
✅ Final Takeaway
Cybersecurity governance is not a technical decision—it’s a leadership responsibility. NIST CSF 2.0 brings this reality to the forefront, offering a framework to lead with confidence.
At Curinovis Digital Agency, we believe that secure operations begin with strategic thinking. Let’s work together to move cybersecurity into the boardroom—where it belongs.
👤 About the Author
Jordan Emanuelson is a Certified Information Systems Auditor (CISA) and cybersecurity strategist. He brings deep experience from KPMG, EY, and the Central Bank as a Regulatory Supervisor. Jordan serves as a knowledge contributor at Curinovis Digital Agency, supporting workshops, training, and consulting programs that merge governance, resilience, and modern security practices.
📩 Contact: info@curinovisdigital.com
© 2025 Curinovis Digital Agency. All rights reserved.

Pingback: Cybersecurity: Strenthening Defenses Through Vulnerability Management and Secure Configurations - Curinovis Digital - Expert Advise